Not Quite Sure.
I know we require information security; however, I’m not sure what we need. I have so many question…
…or I feel like I should if only I knew what to ask.
Take a deep BreAth, you’re not alone.
Everything is difficult until you know how to do it. The same is true for information security and privacy. There are several frameworks that can be applied to help your organization to formalize your approach and ensure a comprehensive outcome. In this section we will look at what we believe are the best approaches and explain some of the solutions, options, prerequisites, benefits, and resource needs. To be honest, everyone’s needs and path are different. So, feel free to schedule a free 30-min session and we can discuss options specific to your needs.
the 27001 standard
The ISO/IEC 27001:2022 standard is the blueprint for a maturing Information Security Management System (ISMS). It consists of two major parts. The management Clauses are sections 4 - 10.2 of the standard and outline the components required to run and maintain the management system and the Annex A controls intended to ensure a comprehensive approach to the mitigation of information security risk.
The newest version of the standard applies the Annex SL approach to harmonize the main components across management systems. This allows for easier integration of additional management systems to the existing structure. One we have often seen is the integration of an Information Security Management System (ISMS) with a Quality Management System (QMS) (ISO/IEC 27001 + ISO 9001). 27001 is also a foundation for additional control frameworks provided by supplemental standards (e.g. ISO/IEC 27017 Cloud Security, ISO/IEC 27018 Cloud Privacy). Additionally, 27001 is required for the implementation of a Privacy Information Management System (PIMS) ISO/IEC 27701 Information privacy.
If you’re looking for an internationally recognized standard that most security questionnaires are based on, this is likely the one for you.
The cost of this certification is highly dependent on the consultant you select, the number of processes being certified, and the number of people within the scope. To be certified you must own a copy of the 27001 standard, and it is not free.
ISO/IEC 27001:2022
Information security, cybersecurity and privacy protection — Information security management systems — Requirements
“It ain’t what you don’t know that gets you into trouble. It’s what you know for sure that just ain’t so.“
– Mark Twain
NIST CSF
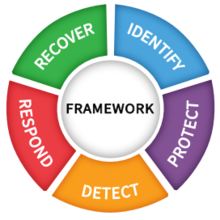
Developed by the National Institute of Standards and Technology (NIST) the Cyber Security Framework (CSF) is an alternative framework for applying information security risk mitigation. It comprehensively addresses 108 controls across five functional areas IDENTIFY (ID), PROTECT (PR), DETECT (DE), RESPOND (RS), and RECOVER (RC). For those looking for evidence of compliance against the NIST CSF standard certifications are available; however, the NIST CSF certifications are non-accredited.
The NIST CSF v1.1 standard is available at no cost
NIST CSF V1.1
Framework for Improving Critical Infrastructure Cybersecurity - Version 1.1
supplementary Standards
Control Frameworks
ISO 27017 and 27018, similar to ISO 27002, provide guidance for the implementation of controls. The supplementary guidance adds new controls or new control requirements to your existing Statement of Applicability (SoA) to address the expanding requirements of the supplementary standards.
ISO/IEC 27017:2015
Information technology — Security techniques — Code of practice for information security controls based on ISO/IEC 27002 for cloud services
ISO/IEC 27018:2019
Information technology — Security techniques — Code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors
Extension to ISO/IEC 27001
ISO 27701 expands the scope of an Information Security Management System (ISMS) adding on a Privacy Information Management Systems (PIMS).
ISO/IEC 27701:2019
Security techniques — Extension to ISO/IEC 27001 and ISO/IEC 27002 for privacy information management — Requirements and guidelines
27001 TOOLKITS
What are toolkits?
Toolkits are a set of premade document templates intended to meet the requirements of the 27001 standard. Essentially, you purchase the document set (i.e., Information Security Policy, Access Control Policy, Statement of Applicability (SoA), etc.).
We tend not to recommend the use of 27001 toolkits…
Auditors recognize the documentation of most major toolkits. To them it can represents a lack of commitment to provide the basic effort and resources required for the successful implementation of an Information Security Management System (ISMS).
The fundamental value of an Information Security Management System (ISMS) comes from its maturity. A management system’s maturity is derived from many aspects of the system that improve over time; the tailored fit of policies, processes, and procedures, the adoption and integration of security into the corporate culture, and personnels’ understanding of their contribution toward security objectives.
Toolkits may be a quick and easy way to get a full set of documents and the structure required for certification; however, the time saved is lost as the toolkit structure repeatedly reinvents the wheel and needs constant overhauling just to work within the organization’s existing security infrastructure.
Redesigning the ISMS once it is in place is not an easy task. Traditionally, companies that have implemented a toolkit have suffered a stunting of the management systems maturity for 3-5 years. Potentially denying their organization the strategic advantage that would have be gained through early implementation of an ISMS.
The fundamental truth is that you cannot purchase the maturity of a management system. Unfortunately, most people who purchase a toolkit find out this truth the hard way. If this does not deter you, lets discuss options, not all toolkits are created equal.